If you happen to uncared for it, on January 22nd The Guardian reported, “Amazon billionaire Jeff Bezos had his cell cellular telephone ‘hacked’ in 2018 after receiving a WhatsApp message that had it sounds as if been despatched from the non-public narrative of the crown prince of Saudi Arabia.”
Constant with the now-contested portray by FTI Consulting cited by The Guardian, that turned into as soon as in April. I turned into as soon as strange ample to investigate cross-take a look at that the “hello boi r u up” texts between Crown Prince Mohammed bin Salman and Jeff Bezos were exchanged sooner than Jamal Khashoggi turned into as soon as murdered in October of that identical year.
Questions, we’ve got got them. But Khashoggi’s name is exhausting to search out in the broader reporting about Bezos’ iPhone — which has been a multitude from the originate up. As a change, a ragged Facebook security pundit and no longer less than one exact researcher snatched the spotlight to claim FTI’s portray turned into as soon as lacking in facts.
The self-appointed infosec “adults in the room” weren’t unsuitable. But it turned into as soon as a pedantic and selfish distraction from the leisure that mattered concerning the entire affair.
Authentic folk salvage out concerning the perchance hacking of Bezos’ cellular telephone and shrugged. He can come up with the cash for the finest security on this planet. Saudi Arabia’s Prince Claus von Bonesaw is a monster. All people’s getting hacked, particularly us peasants. These are all issues we all know.
What we furthermore know is that the supposed cellular telephone hack came by approach of an attachment. And if the hack took space, an attachment turned into as soon as clicked. It be the identical contrivance the Metropolis of Baltimore’s computer programs and emergency programs at Hollywood Presbyterian Properly being facility were contaminated and locked with ransomware. And it be how shoppers are losing identities and accounts from malware, discovering out strategies to send Bitcoin to grubby teenage boys in latitudes and longitudes unknown due to ransomware. Click a hyperlink. Take a look at at an attachment. Catch a file. That’s it. An attacker went phishing, and now you is liable to be on the hook.
All that is from phishing, although what we hear about most are the breaches: attackers grabbing usernames and passwords from breach dumps, then the use of instruments with cutesy names love SNIPR or STORM to automatically strive it out to your entire accounts to glimpse what works. Which they attain, on narrative of Equifax frail default passwords on ravishing files, Facebook turned into as soon as so busy lying to everybody it left the barn doors launch and the Metropolis of Aloof Orleans refused to imagine cybersecurity is excessive infrastructure.
So worthy for “the adults in the room.”
I attended a recent hacking conference in San Francisco known as Disclosure searching forward to masses of the identical original hells — the “I’m smarter than you” guys competing for consideration whereas anxious researchers in the background are attempting to teach us one thing’s on fireplace.
I turned into as soon as no longer upset.
Apropos to what turned into as soon as going down (or no longer) to Jeff Bezos at that moment, I noticed the controversy “Preliminary Public Ownage: Developments in Phishing Tactics All over Refined Risk Actors.” Sounds dumb, exact? Nope.
Constant with jaw-losing files equipped by Proofpoint’s Ryan Kalember, phishing is now the No. 1 attack of different for cybercriminals. “Phishing is stunning for a entire lot of causes for the attackers that attain maintain technical skills, on narrative of it scales undoubtedly properly,” Kalember told Engadget by approach of electronic mail. “The larger teams, love the risk actor in the motivate of Emotet, maintain built the automation to realize social engineering on the dimension of millions of messages a day, and are very lawful are getting their fairly easy assaults (continuously documents with macros despatched by approach of already phished cloud electronic mail accounts) by security controls.”
So what, you relate? The entire adults (who were in the room a minute ago) know now to no longer click on irregular links to discover a free iPad or log in at notgoogle.com or accumulate the attachment from Lisa@FreePills. Who does that? Florida grandmas falling for Nigerian princes, indubitably.
This thinking is okay and lawful totally beneath the arrogance that getting pwned is for those who attach no longer appear to be as stunning as you or that the cliques working security for your electronic mail potentialities maintain perfected their specious and occult magics of marking suspicious emails with gigantic, elephantine, crimson DANGER warnings. The adults maintain it beneath alter, you imagine. Gosh, there should be masses of boring folk, you muse.
Turns out, you is liable to be relatively unsuitable on every counts.
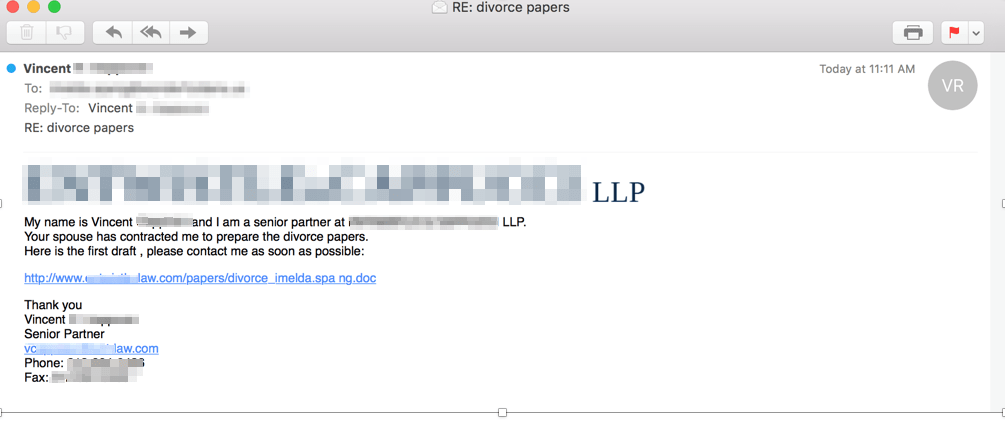
If you happen to bought an electronic mail from a law firm asserting “divorce papers” and it turned into as soon as a exact law firm and the electronic mail contained a hyperlink to a doc on that net net page, you would doubtlessly maintain a extremely emotional reaction and click on on it. Kalember noticed masses of examples and introduced receipts.
“On the entire,” Kalember explained to Engadget, “the sneakiest phishes are highly socially engineered and customised for a particular supposed recipient. The finest example is a criticism a pair of particular person, despatched to that person, which threatens to electronic mail (or even straight cc’s) their supervisor. That talked about, we’ve got considered risk actors use all the issues from fraudulent food poisoning complaints, Greta Thunberg pledges, and Christmas celebration invites in barely the closing couple of months, so there is no shortage of innovation.”
Excellent now spherical 1.3 million phishing operations live illicitly on spherical 300,000 URLs. Somehow it skill many other folks shall be hacked/attacked on narrative of any person else’s net net page security sucks.
So are all those WordPress hacks and vulns adding up or what? Kalember told us, “Compromising WordPress and other sites is unfortunately somewhat overall, and it can well maybe also be no longer easy for even the most experienced administrators to entirely stunning as attackers continuously possess layers of entry.” Explaining further, he added, “A trim amount of malicious inform material is furthermore hosted on cloud file storage that just about all networks (and users) want to have confidence: SharePoint and OneDrive are the finest offenders for the time being.”
Each net net page that would possibly maybe also furthermore be compromised — hacked into — is being frail to send legitimate-taking a spy phishing emails, the use of mail addresses from net sites starting from alpaca farms to law companies to universities.
Dawdle, exact alpaca farms. “Whereas it be that that chances are high you’ll also imagine that the North Korean risk actor in request has a technique of humor,” Kalember talked about, “it turned into as soon as a WordPress space that turned into as soon as weak to an customary exploit, so it turned into as soon as doubtlessly exact opportunistic. From a network level of view, no one is liable to block their users going to alpaca farm net sites, so it suits their capabilities for teach and alter of their malware.”
Criminal organizations are compromising legit sites and the use of those to send legit (and despicably personal) phishing assaults to install malware or ransomware. Frequently they’re searching to compromise your employer or make a selection your accounts, on narrative of those are extremely treasured for doing extra crimes. More to the level, thinking that you is liable to be no longer a target for any motive (“I’m no longer that appealing” or “I manufacture no longer maintain followers/cash” or “my job is dumb”) goes to originate you the suitable target.
And taking a spy at infosec traits (which have a tendency in direction of sensationalism and know-it-alls), there is a main lack of adults in the room to look our backs. Kalember told Engadget, “Merely acknowledged, attackers center of attention on folk, and most defenders don’t. Boosting consciousness and electronic mail security controls are two perfect techniques to vastly reduce risk.”
A vivid and prophetic TV sign known as The X-Recordsdata as soon as talked about, “Trust no one.” This has never been truer than now. As antagonistic to alarm about every provoking electronic mail or textual inform material message, treat your entire inboxes love your front door: If you happen to is liable to be no longer searching forward to a offer, don’t launch the door.
Photography: AP Describe/Ted S. Warren (Jeff Bezos); Proofpoint (Malware electronic mail)
On this text:
Snide Password, badpassword, commercial, files breach, Facebook, gadgetry, objects, gear, hacks, infosec, net, jamal khashoggi, Jeff Bezos, cell, idea, phishing, phishing scams, Proofpoint, ransomware, security, services and products, WhatsApp, wordpress
All merchandise advisable by Engadget are chosen by our editorial personnel, just of our parent firm. A couple of of our reviews contain affiliate links. If you happen to desire one thing by one of those links, we’d also sign an affiliate fee.

291
Shares
P&T, consultation, engagement, property development, planning permission, council permission, planning law, planning application, public consultation, public engagement,Phishing,scams